What is Carding and How to Prevent it in Your Online Store

This year, experts expect the total global card loss to exceed $35 billion. As the number of card holders increases, so does the amount lost to fraudulent transactions. In 2019, for instance, for every $100 sale, almost $6 was lost to fraud. The losses stemmed from counterfeiting, card-not-present (CNP), fraudulent application, lost and stolen card, card-not-received, and other fraud categories.
Like most cybercrime forms, card fraud can be avoided with the help of technologies such as IP Geolocation API or IP Geolocation Database. We’ll discuss how in more detail later. First, let’s define carding, which accounts for much of the card fraud we have seen.
What Is Carding?
Carding is defined as the illicit use of a payment card, regardless of type—credit or debit—by unauthorized users or carders to buy a product or pay for a service. Carders can obtain payment card information in various ways: either steal credit card credentials from the users themselves or buy so-called “fullz” files on the Dark Web.
Fullz is the hacker term for a package containing the full set of personally identifiable information (PII) that cyber thieves can use to commit fraud. Carding requires the stolen cardholder’s name, birthdate, complete address, Social Security number, account number, card verification value (CVV), and other data. A fullz file typically sold for $4-10 in 2019 on the Dark Web.
How Do Cybercriminals Perform Carding?
Hackers often use various tools and tactics to steal victims’ payment card credentials. Here are four of the most common carding means:
1. Malware Attacks
Spyware designed to record keystrokes and steal usernames and passwords saved in browsers helps carders obtain the information they need to commit card fraud.
2. Phishing Campaigns
Carders typically send victims phishing emails supposedly from their credit card issuers to trick them into sharing their personal and payment card information. These days, however, cyber thieves can use other phishing mediums, including phone calls (via the so-called “vishing”), text messages (“smishing”), social media direct messages, and even postal mail.
3. Carding Forums and Underground Markets
Carding forums and underground markets are typically found on the Dark Web. These are illegal websites where cybercriminals buy and sell fullz files, exploits, and malware. Bad guys also share ways to steal financial details here. They can also test stolen card information on these sites.
4. Skimming Attacks
Card skimmers are small, hard-to-spot devices that thieves install on legitimate payment card readers or point-of-sale (PoS) systems. When cardholders slide their cards on compromised PoS devices, the card skimmer reads and sends their card information to the criminals.
How to Protect Your Organization and Customers from Carding
Apart from educating end-users or customers on carding and its dangers, online shops can do more for fraud protection. Integrating an IP geolocation API into payment gateways can reduce instances of fraud. IP geolocation solution integration can particularly:
1. Match a User’s Current Location to His/Her Billing Address
Research reveals that CNP fraud is more likely to occur than PoS fraud. Most carders also prefer to buy products or pay for services with stolen payment cards online rather than in person. That reduces their chances of getting caught red-handed.
But there is a way to spot CNP fraud as it happens with the help of IP geolocation. Remember that any person’s physical or billing address should match his/her IP address somewhat. Any online shop owner or administrator can catch a fraudster by checking if his/her IP geolocation during the transaction matches the registered shopper’s records.
For example, imagine that a supposed regular U.S-based Amazon shopper bought a smart TV with his/her credit card. While he/she gave the right credentials, the shop owner or administrator can still do an additional check to ensure the transaction is legitimate. If the shopper lives in Texas and your network logs revealed his/her usual IP address as 192[.]227[.]139[.]106 but the current transaction is coming from 88[.]26[.]241[.]248, the shop owner or administrator should flag it as suspicious. Our IP Geolocation API query for 88[.]26[.]241[.]248 revealed that the user is from Andalusia, Spain.
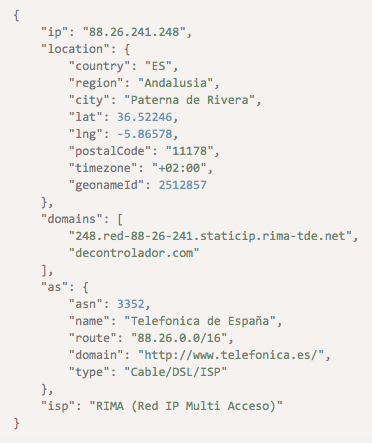
With IP geolocation’s help, users can stop a potentially fraudulent transaction as it happens. Unless the cardholder is currently traveling to Spain, which can be confirmed via a phone call, the shopper pretending to be him/her won’t be able to charge an unauthorized payment on his/her card.
2. Keep a Closer Eye on Card Transactions Made from High-Risk Locales
A study revealed that card fraud is particularly prevalent in Brazil, followed by Mexico and Russia. These nations were identified in 2016 based on chargeback computation rates. Brazil, which topped the list, had a chargeback rate of 3.55%, which meant that around four out of every 100 transactions made from the country are fraudulent.
Given a list of high-risk countries, online shop owners and administrators can make it a point to pay closer attention to card users from the identified countries. We know that we can locate every user’s country via his/her IP address. Shop owners and administrators can, for instance, require card users in high-risk locales to use multifactor authentication (MFA).
Given that, a Brazil-based IP address such as 179[.]93[.]224[.]125 should, at the very least, trigger an alert for further authentication on the part of an online shop that implements IP geolocation-based security.
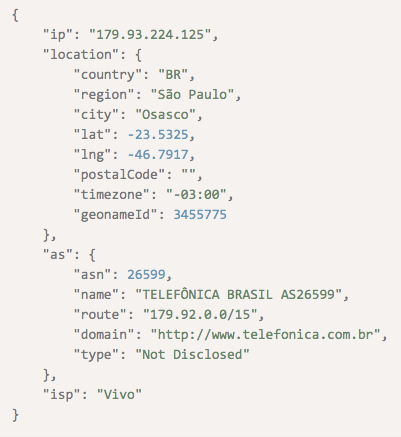
The shop owner or administrator can ask the cardholder to provide additional proof of identification or authentication to prevent fraud.
3. Watch Out for Known Card Fraud Indicators of Compromise (IoCs)
It has become common practice for organizations, both public and private, to publicize IoCs attacks in news, blog posts, and even databases. Sharing this information allows businesses and individuals alike to steer clear of threats that can put them at risk of financial and data theft.
Publicly accessible IP address databases such as the one that AbuseIPDB maintains can help users, including online shop owners, to block all potential threat sources from gaining access to their networks.
Knowing that the IP address 171[.]221[.]241[.]89 has been cited for malicious activity 201 times on AbuseIPDB, for instance, can allow an IP geolocation-enhanced payment gateway to block any transaction coming from it. The enhanced solution should get this information from IP Geolocation API:
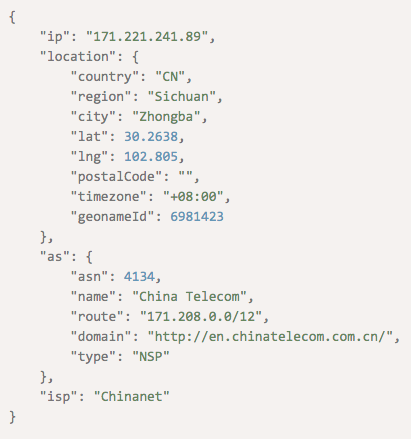
Note how the details from the API match those given on the AbuseIPDB page for the IP address.
---
Carding significantly compromises not only cardholders but also online shop owners. E-commerce businesses not only stand to lose their customers’ trust but also profits that otherwise go to chargeback payments and in cases where litigation occurs, settlements. Digital entrepreneurs won’t have to suffer if they add an IP geolocation solution to their payment gateway security stack.