IP Geolocation Database: How to Use It to Prevent Media Theft

Media theft is every streaming and content provider’s nightmare. And that’s not surprising given that practically all movies, TV shows, or songs have been downloaded illegally at least once. That translates to lost income not only on the streaming provider’s part but also on that of the content’s creator.
Over time, in fact, we’ve witnessed several big names suffer from media theft with disastrous consequences. We named a few high-profile cases below.
Infamous Media Theft Cases
Many movies are made available on various peer-to-peer (P2P) sharing networks or what are more popularly known as “torrent download sites.” That automatically spells lost revenue for their owners but things get so much worse when they are leaked even before they are shown in theaters. We listed three of them below, along with their respective repercussions to their owners.
Sony Pictures Entertainment Hack
The hack reportedly began as a form of retaliation against offending content in the movie “The Interview.” The hackers warned the company that it would leak its upcoming films if the said movie was released to the public. The company’s computers were locked with a wallpaper featuring a neon red skeleton and a threat that its data will be released if it doesn’t do as told.
In the following weeks, Sony Pictures Entertainment's stolen data was leaked. This included movies that were yet to be shown in theaters, such as “Fury,” “Annie,” and “Mr. Turner.” All in all, the three movies alone were downloaded by around 1.5 million unique IP addresses.
Park Jin Hyok, the man allegedly responsible for the hack and the WannaCry outbreak, has been incarcerated ever since.
Expendables 3
The third part of the Sylvester Stallone action movie series was leaked online three weeks before it premiered. According to reports, it was downloaded around 2 million times (cost around US$16.3 million) before it even came out in theaters.
Luqman Farooq, the person behind the theft of this and other movies and TV shows was jailed for more than two years after being found guilty of the crime. He was part of a network that copied 25,000 movie and TV show files for illegal distribution.
Star Wars Episode III: Revenge of the Sith
While this movie was hacked when we were all still using dial-up connections and distributed by an employee, its release an hour before it was shown remains illegal. It was downloaded at least 16,000 times before its source, the house of hacker Marc Hoaglin, was traced and he was apprehended.
Hoaglin pleaded guilty and spent a month in jail along with seven other pirates.
These hacks are just three of the many that occur every single day. And movies and TV shows are not the only kinds of intellectual property that get stolen. Media theft is, however, avoidable through a variety of mechanisms. One of the ways to do that is by using reliable IP geolocation tools. The next section shows how.
How to Use IP Geolocation Tools to Prevent Media Theft
An IP geolocation database can help content owners protect their intellectual property from theft in various ways. Three of the most common are listed below.
Disallow or Limit Downloads
These days, one of the most effective ways to limit the spread of illegal content copies is by offering subscriptions instead of downloads. It’s not as easy to distribute streamed content as opposed to file downloads, after all.
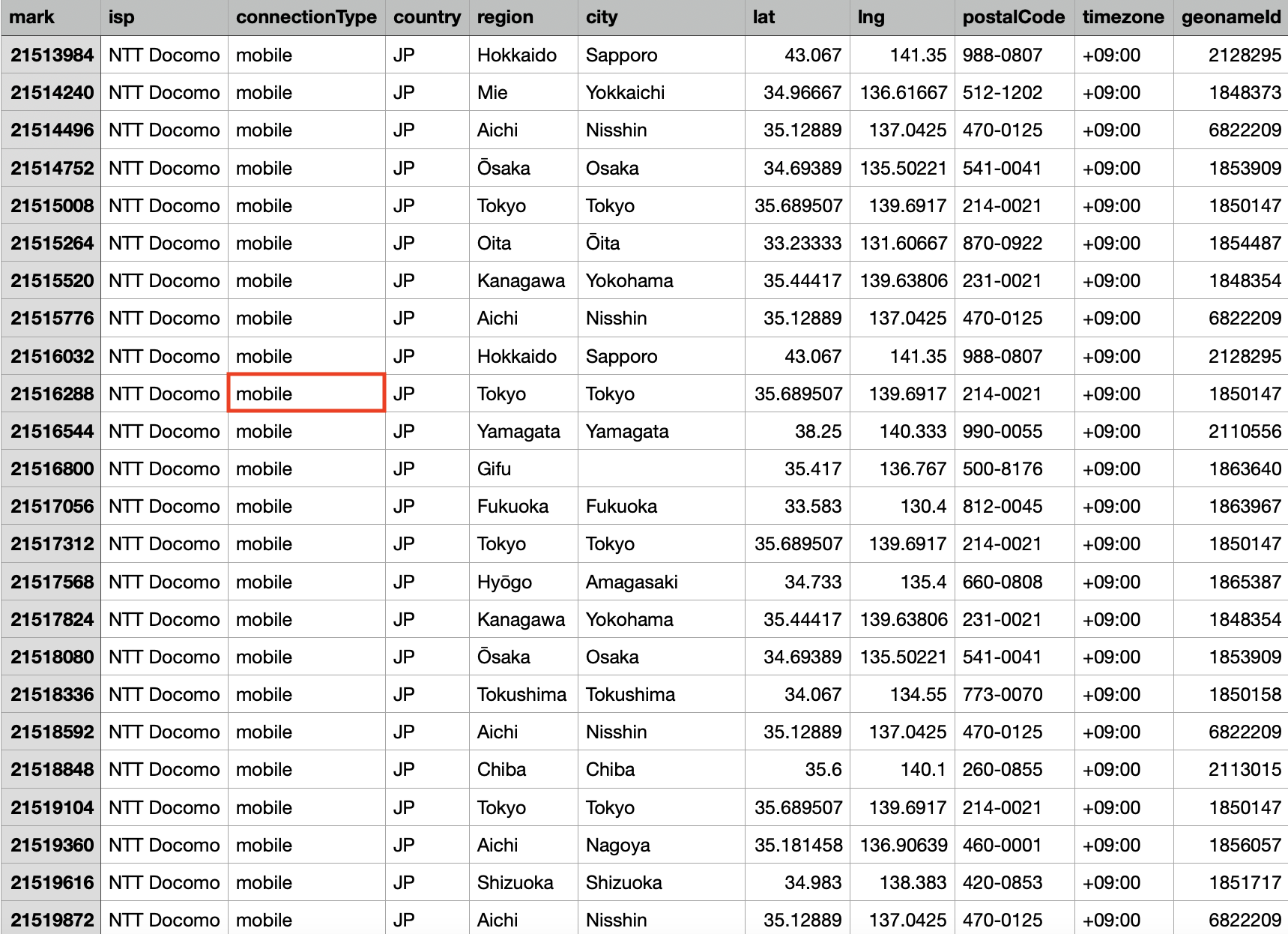
Streaming service providers limit the number of users or devices that can log in using a subscriber account. Netflix, for instance, only allows a maximum of four devices to watch content on at the same time or download content to (for watching offline) with its Premium plan. It’s safe to assume that it tracks user devices via their IP addresses since it typically warns subscribers each time a new device signs in to their accounts via text messages and emails. These warnings even tell you what kind of device signed in to your account, information that’s available in an IP geolocation database.
Allow Only Account Owners to Access Content
Another method to prevent media theft is by allowing only legitimate account owners, tracked via their recorded IP addresses, to access content. For this, you would need to keep a database containing your customers’ account credentials (names, contact details, payment credentials, etc.), including their IP addresses.
Each time they sign in to their accounts on your website, their IP addresses get logged. You can then compare the logged-in IP addresses with their usual login data (their IP addresses on record). If these don’t match, there’s a good chance someone else is using their accounts. If they didn’t authorize anyone else to access their accounts, you could be dealing with a cybercriminal out to steal intellectual property.
Cybercriminals, most certainly, won’t sign up to your service with their own credentials. That would make it so much easier for law enforcement to track them down and catch them red-handed. They would instead hack into legitimate subscribers’ accounts and siphon off data through these.
Prevent Proxy Users from Accessing Content
As an added precaution, it’s typically the norm for media thieves to hide behind proxy services to mask their identities. While most IP geolocation databases won’t readily identify proxy, virtual private network (VPN), and Tor users, there are tools that can do so.
One option is to download an IP proxy data feed. If the IP addresses currently accessing your content are in the feed (belong to proxy, VPN, or Tor users), you can configure your network to disallow them from even logging in to your website. That can help limit the number of potential illegitimate users from stealing copyrighted materials.
Another option is by integrating a VPN and proxy detection API into your system. This tool identifies if an IP address belongs to a proxy, VPN, or Tor user, which should also help reduce the number of unwanted users in your network.
Both the proxy data feed and API would tell you if an IP address that’s logged in to your site belongs to a user who’s masking his/her identity. Here’s a sample result from the API:
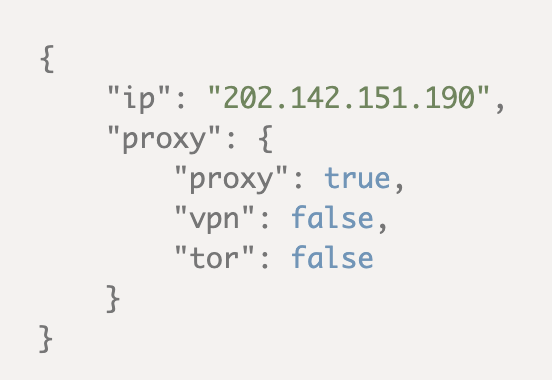
Note, however, that not all proxy, VPN, and Tor users are threat actors – some are regular users who just want to protect their privacy online. Still, if you wish to limit your exposure to digital piracy, you can warn potential subscribers from the onset that you discourage proxy, VPN, and Tor users from signing up for your services.
---
While using an IP geolocation database is not a foolproof means to prevent media theft, it is a step in the right direction. With its help, you can at least lessen your exposure to illegal downloads and fake subscribers. You will you be protecting not only your intellectual property, but your subscribers’ accounts, too.