How to Locate and Stop Phishing Threats Using IP Geolocation

While phishing is no longer a new thing, it remains a huge threat to organizations worldwide as these statistics show:
- Phishing accounts for more than 80% of the total number of reported security incidents, and victims lose as much as $17,700 per minute due to the threat.
- Targets open almost 30% of phishing emails.
- In 2019, around 33% of data breaches involved phishing or some form of social engineering.
- As many as 65% of targeted attack groups accomplish their goals via spear-phishing emails.
- Around 56% of decision-makers believe that phishing is a top security threat.
- Almost 1.5 million phishing sites are created each month.
- Each user can receive as many as 16 phishing emails each month.
- A medium-sized company could lose as much as $1.6 million to a successful phishing attack.
The data presented above are just some of the reasons why companies, regardless of size, need to stay protected from probably one of the oldest yet still active threats—phishing. This post features an oft-unused means by cybersecurity teams to effectively stop phishing threats—IP geolocation.
4 Ways Cybersecurity Teams Can Use IP Geolocation API’s Data to Stop Phishing Threats
IP Geolocation API identifies the geographic location of any user given his/her IP address. While many cybersecurity teams may not often use it as a means to stop phishing threats, integrating the API into existing security solutions may help. Here’s how:
1. Keep Phishing Emails Out of Employees’ Inboxes
Phishing emails are a dime a dozen. Phishers are known for using up-to-date and relevant social engineering lures to get potential victims into divulging personally identifiable information (PII), including their online account credentials. And once they have those at hand, they’re just a step away from stealing their victims’ savings or getting access to their corporate accounts. The latter, of course, provides more significant payouts to phishers.
That is why it is good security practice to keep an eye on the IP addresses of all entities your company does business with. Integrating IP Geolocation API into your email security solution can alert you to unknown IP addresses that can quickly turn into threat sources.
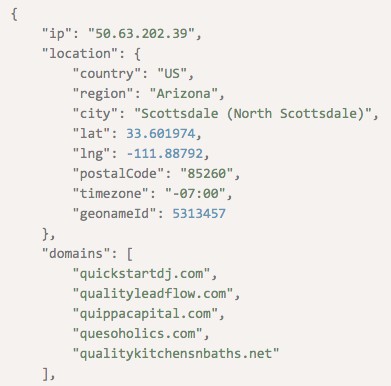
Let’s say, for example, that one of your employees is alerted to an alleged email from your bank (e.g., Chase Bank) concerning a company loan payment. That message came from the IP address 50[.]63[.]202[.]39. A check against your authorized list of IP addresses or whitelist may confirm if it is trustworthy. An IP Geolocation API-enhanced email security solution can at least alert the recipient about the message.
You can also run it through the IP Geolocation API for further scrutiny to double check that you’re not blocking one of your bank’s IP addresses. Our API query revealed that 50[.]63[.]202[.]39 is not connected to Chase Bank. Instead, it has ties to several domains including quesocaciquedip[.]mobi, qualityleadflow[.]com, quippacapital[.]com, quesoholics[.]com, and qualitykitchensnbaths[.]net. A Web search for it also showed that it has been reported for varying malicious activities eight times.
2. Avoid Business Dealings with Fraudsters
A good business is one that protects not only its assets but also its clients. After all, you can’t maintain customer loyalty if phishers can easily exploit your websites to steal from your customers.
Take an e-commerce business as an example. We’ve seen phishers who managed to obtain victims’ credit card details use these for card-not-present (CNP) fraud. Companies that employ IP geolocation checks before concluding online transactions can avoid this threat.
A simple comparison of the cardholder’s geographical location while making a purchase with that on record may put an end to an incident. That way, the e-commerce platform not only saves the customer from paying for something a fraudster ordered but also gains that client’s trust.
3. Prevent Your Company from Becoming an Invoice Scam Victim
There are various types of phishing, one of which is business email compromise (BEC). BEC attackers typically use fake invoices to steal money from target companies. They generally pose as a supplier, often even hijacking ongoing email threads to provide a semblance of legitimacy to their scams.
Let’s say, hypothetically, that your manufacturing company obtains many of its raw materials via a large online supplier called AmazingSupplies. But since you’re a returning customer, AmazingSupplies bills you each month instead of per order. That said, your finance department gets an invoice monthly.
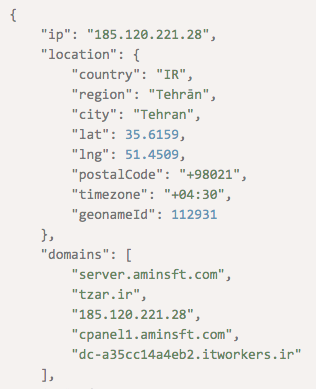
While processing invoices for the past month, a finance staff member was alerted to a suspicious invoice email. The sender’s IP address 185[.]120[.]221[.]28 didn’t match any of those that the supplier owns.
The right way to go about this is to validate his suspicion. And there’s a quick means to do that is by running an IP Geolocation API query for the IP address in question.
As it turns out, the user of 185[.]120[.]221[.]28 is based in Tehran, Iran. AmazingSupplies, on the other hand, typically uses U.S.-based IP addresses. And as a well-established entity, the online supplier probably doesn’t use IP addresses shared with other domains — unlike the IP address cited, which shows a list of connected domains in the below screenshot. A Web search (enclosed in quotation marks, so you don’t accidentally access a suspicious site) for the IP address also revealed that it had been reported as malicious more than 1,300 times. Therefore, it would be safe to assume that the address doesn’t belong to AmazingSupplies and is malicious, so it should be blocked.
In this case, a check via IP Geolocation API just saved your company from paying phishers a potentially large sum.
4. Create a Phisher’s Profile
An IP address can reveal more about a user than just their geographical location. When queried through IP Geolocation API, you can also get a list of connected domains, its registrar, and connection type. When investigating a phishing attempt or attack, that information may prove useful.
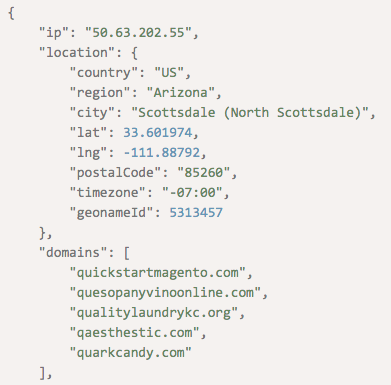
Let’s say that you were the recent target of a phishing attempt that your security team thankfully averted. But all the analysts obtained was the phisher’s IP address—50[.]63[.]202[.]55. You no longer want to suffer the same fate in the future, of course, and so you decide to find out more about the attacker.
You can start by querying the IP address on IP Geolocation API. The results revealed that it has ties to the domains quickstartmagento[.]com, quesopanyvinoonline[.]com, qualitylaundrykc[.]org, quarkbomb[.]net, and quarkcandy[.]com. You can create a profile of your phisher to identify other potential threat sources given that information. You can obtain the domains’ owner information via WHOIS lookups and proceed from there. If any of the domains or their owners prove malicious, add them to your blocklist, too.
---
When dealing with fraudsters and cybercriminals, IP geolocation data can be a handy resource for cybersecurity teams who want to eliminate phishing threats.