How IP Geolocation Can Improve Your Defense in Depth (DiD) Strategy

The latest stats reveal that a cyberattack happens every 39 seconds worldwide. Therefore, it isn’t surprising why cybersecurity experts say that one single approach to cyber defense is no longer enough. These days most cybersecurity solution providers tout the use of multilayered defense or employment of the so-called ‘defense in depth’ (DiD) strategy.
But what is a DiD strategy? Do organizations really need it? And how does an IP geolocation database figure in it? This post will discuss the answers.
What Is DiD?
DiD is a cybersecurity approach that layers multiple defensive mechanisms to protect valuable data. A DiD strategy thus employs intentional redundancies to enhance the security of a system by addressing all potential attack vectors.
A typical DiD-enabled network setup would look something like this:
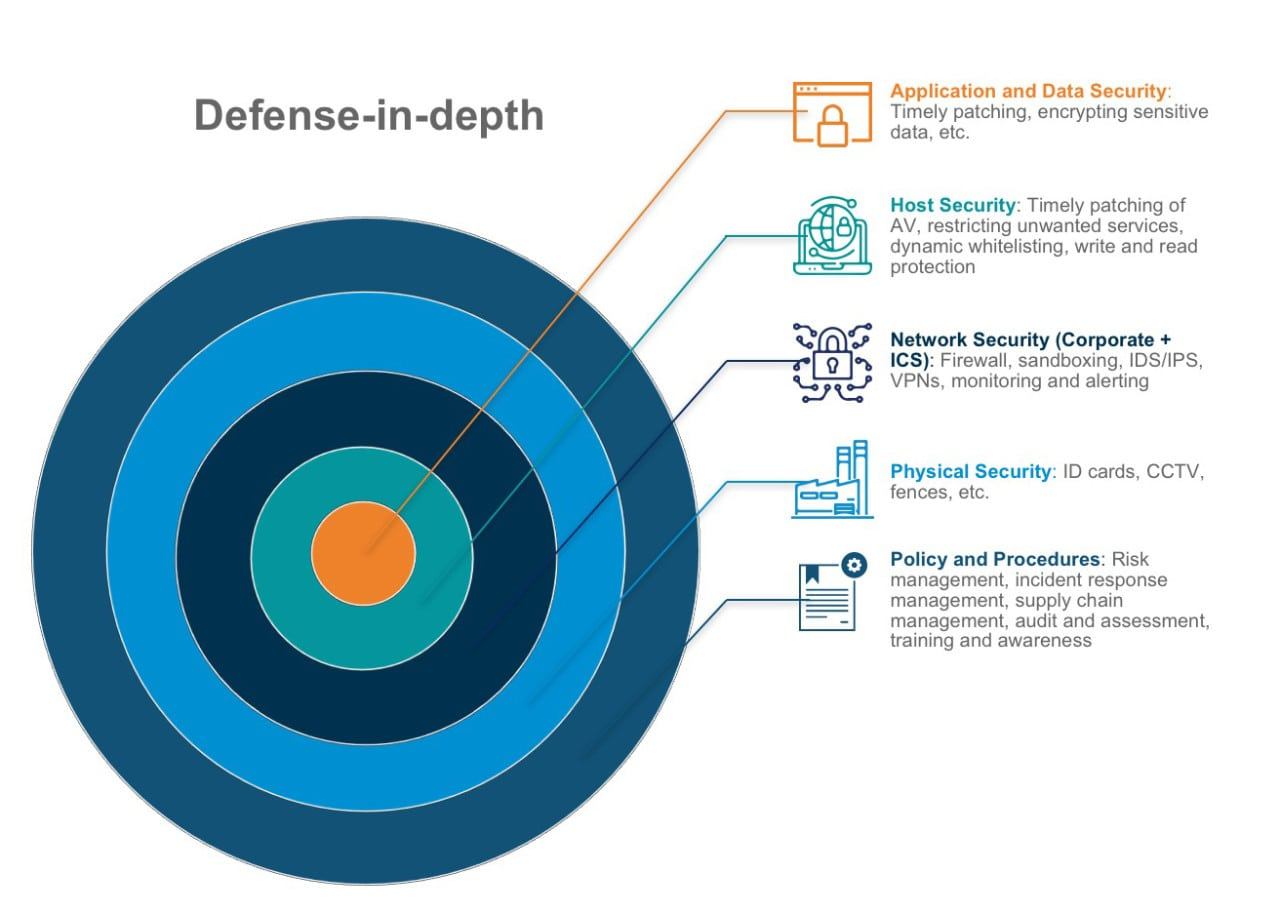
In a nutshell, a DiD strategy layers all kinds of security policies, protocols, solutions, and systems on top of each other to keep confidential data and critical systems safe from both physical and virtual attacks coming from within and outside the network. This approach has given birth to tech jargon that you may hear from cybersecurity solution experts like “holistic cybersecurity” and “multilayered defense/security.”
What Elements Make Up a DiD Strategy?
As shown in the diagram above, a typical DiD strategy comprises five components—policies and procedures, physical security, network security, host security, and application and data security.
None of the defenses a company puts up will work unless all of its employees comply with security policies and procedures. That makes training and strict implementation a must. Only by avoiding potential threat sources can an organization indeed become resilient to attacks.
Let’s face it, no matter how many security solutions an enterprise uses on its systems, they will be no match when attackers gain physical access to their storage devices. Armed with the right credentials (usernames and passwords), threat actors can easily break into even the most sophistically encrypted corporate system, which they can obtain by stealing a laptop with the right level of user access rights. And if the malicious actor is an insider, then hacking becomes even easier.
Policies and procedures and physical security are just the tip of the iceberg, though. To make DiD work, a company needs to protect against all kinds of online threats from the network, host, and application and data layers.
To keep external threats out, organizations need to use firewalls, sandboxes, intrusion detection/prevention systems (IDSs/IPSs), virtual private networks (VPNs), and a variety of monitoring and alerting tools at the network layer. These solutions filter known indicators of compromise (IoCs) as soon as they attempt to access any network-connected system.
Again, today’s threats are becoming stealthier by the minute. And those that make it past a company’s network defenses (unknown threats) must be prevented from making unauthorized changes to system settings. That is where host security comes in. It ensures that only authorized users can access internal systems and data through antimalware, blocking unwanted services, whitelisting, and access rights management (ARM).
If all else fails, an organization can still protect its crown jewels from breach or theft through application and data security. It can employ multi-factor authentication to protect systems and encryption to safeguard confidential data.
All these layers work hand in hand to ensure the security and integrity of a network at all times.
Who Can Benefit Most from a DiD Strategy?
Experts opine that industrial control systems (ICS) operators are particularly in need of DiD. While many of them still enforce “security by obscurity” by keeping their most critical infrastructure disconnected from the Internet, infamous attacks like Stuxnet in 2010 and Duqu in 2012 showed that the approach is not foolproof.
These incidents contributed to the growing use of DiD strategies in several industries that include but are not limited to the government, financial services, and IT. Practically every organization that deals with sensitive information can benefit from multilayered threat defense.
What Can an IP Geolocation Database Contribute to a DiD Strategy?
While an IP geolocation database may not be as useful when it comes to maintaining physical security, it does serve several purposes in network, host, and application and data security.
Network Security
IoC lists typically include malicious URLs and IP addresses, malware, and command-and-control (C&C) server addresses. And so, as an additional security layer to prevent unwanted network access, companies can use an IP geolocation database to verify users before granting them access to network resources.
By limiting access to IP addresses that belong to authorized users (customers, partners, and other third parties), you significantly reduce your chances of interacting or communicating with threat actors. Immediately rejecting connections, for instance, from devices whose IP addresses aren’t in your “allow” list can significantly reduce attack attempts.
Network intrusion attempts, meanwhile, from known threat sources are thwarted quickly. IP addresses that have been flagged “malicious” are automatically denied access, thus saving you from a potential breach.
Here’s an example. We learned that the IP address 5[.]196[.]70[.]107 had been reported 9,842 times by 533 distinct sources for ties to multiple brute-force attempts. We can thus assume that it is indeed malicious.
IP Geolocation Data Feed provides these details about 5[.]196[.]70[.]107:
- Country: France
- Region: Hauts-de-France
- City: Gravelines
- Latitude: 50.9871
- Longitude: 2.12554
- Postal code: 59820
- Time zone: UTC+02:00
- GeoNames ID: 3014816
- Domain: ns379769[.]ip-5-196-70[.]eu
- Autonomous System (AS) number: 16276
- AS name: OVHcloud
- AS route: 5[.]196[.]0[.]0/16
- AS domain: http[:]//www[.]ovhcloud[.]com
- AS type: Content
- Internet service provider (ISP): OVH SAS
Before the attacker can even cause damage to your network, include 5[.]196[.]70[.]107 in your blocklist at once. Publicly available blocklists like AbuseIPDB can guide you on the most destructive IP addresses to ban from your network. As an additional precaution, you can even include associated domain names such as ns379769[.]ip-5-196-70[.]eu in your blocklist.
Host Security
Any IP address that bypasses an enterprise’s network security can still be denied access at the host level. Limiting access internally can further reduce risks.
An IP geolocation database can help you better contextualize the list of all the IP addresses assigned to your company and partners. By only allowing those within your IP range to access internal systems, you limit data exposure to authorized users.
Let’s look at a hypothetical scenario. Say, you work as an IT security specialist for Google. Then you would have a list of all of the IP addresses its employees use. You were alerted when the IP address 112[.]85[.]42[.]186 tried to log in to an internal system.
While it’s possible an employee who’s currently working remotely and failed to use the corporate VPN is the one attempting to access an internal computer, you can’t be sure and just let it bypass security. A web search for 112[.]85[.]42[.]186 would reveal that it’s been cited for various malicious doings 14,320 times. Now it’s safe to block it because it’s highly likely to be dangerous.
Application and Data Security
Let’s say for demonstration purposes that the threat to your corporate security comes from an insider. However, because of stringent physical security measures, the attacker can’t get to the actual device he/she wants to break into. He/She has no other possible course of action but to use his/her own workstation.
While the attacker’s IP address may not trigger network and host alarms, it may not be authorized to access a highly secured database. Therefore, any attempts to log into the said database using his/her computer will still trigger an application-level alert, putting a stop to the attack.
Here’s how an IP geolocation database can help. Using the same Google example as above, let’s assume that 172[.]217[.]0[.]10 is trying to access a highly sensitive database. While the IP address isn’t malicious and Google-owned (as the IP geolocation details below reveal), it isn’t part of the IP range (e.g., 64[.]18[.]0[.]0–64[.]18[.]15[.]255) that’s authorized to view the database in question. Hence, it is safe to continue denying the IP address’s access. Investigating the motives of 172[.]217[.]0[.]10’s owner may also be a good idea.
- Country: U.S.
- Region: Illinois
- City: Chicago
- Latitude: 41.8781
- Longitude: -87.6298
- Postal code: 60666
- Time zone: UTC-05:00
- GeoNames ID: 4887398
- Domain: ord38s04-in-f10[.]1e100[.]net
- AS number: 15169
- AS name: Google LLC
- AS route: 172[.]217[.]0[.]0/24
- AS domain: https[:]//about[.]google/intl/en/
- AS type: Content
- ISP: Google LLC
---
As we’ve seen, no one security solution can adequately protect an organization. To effectively thwart attacks and attempts, a combination of several solutions, including IP geolocation, is critical. Enhance your DiD strategy with the help of a comprehensive IP geolocation database.